
A visit to our LogRhythm web page suggests that Cyber Risk Visibility, Rapid Mean-Time-To-Detection (MTTD) and a reduction in Mean-Time-To-Recovery (MTTR) are significant cyber threat issues that you wish to tackle now.
LogRhythm specifically formulated its technology to provide Organisations with the ability to seek out CYBER MENACES, rapidly identify them and neutralize the hazards; fast. It's unified platform succeeds and refashions Security Operations and the skill in dealing with Cyber Menaces, delivering a big-picture view (for the prioritization of the right responses), accurate response data, evidential and actionable intelligence.
to email for further assistance or to arrange an appointment.
Alternatively call our office number +44 (0)1344 780000.
Security Information and Event Management (SIEM) technologies are designed to meet an Organisation's need to analyse in real-time Event Data for the early detection of targeted Cyber Attacks and Data Breaches. Furthermore, SIEMs need to capture, store, examine and report on Log Data for Incident Response, Data Forensics and Regulatory Compliance.
In general, SIEM technologies aggregate event data extracted from Applications, Security Devices, Network Infrastructures and Systems. The main source of a SIEM's information is Log Data, however it can also process other forms of data i.e. from NetFlow and Network Packets.
In operation the SIEM's event data is combined with contextual information about Users, Assets, Threats and Vulnerabilities. That Data is then normalized so that events, contextual information and data from it's various sources can be correlated and analysed for the purpose of Network Security Event and User Activity Monitoring and Compliance Reporting.
Finally, SIEMs provide real-time correlation of events for security examination, querying and analytic purposes for Historical Analysis and to support Incident Investigation and Compliance Reporting.
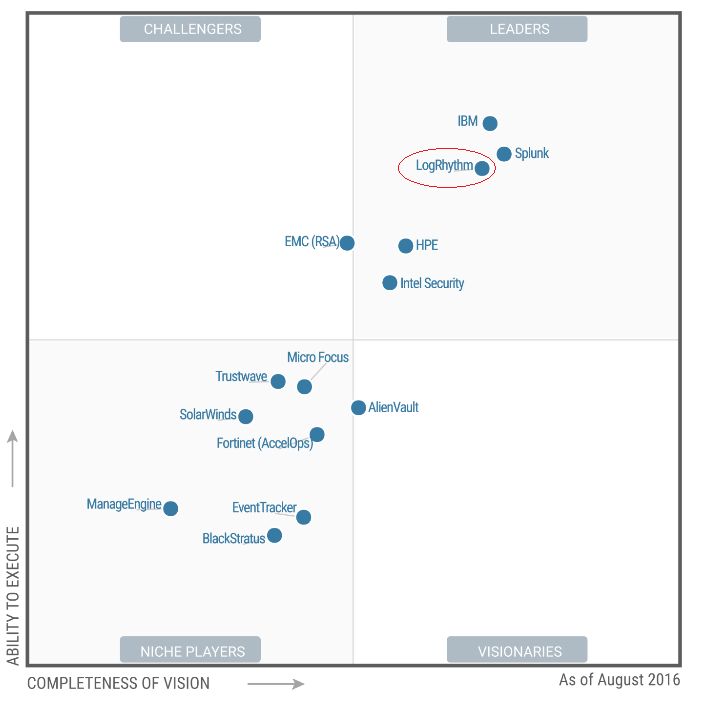
LogRhythm's SIEM technology achieves the above functionalities and is an ideal solution for midsize and large Organizations. It's market recognition is demonstrated by the "market leader" position it occupies in the Gartner Magic Quadrant graph shown to the side.
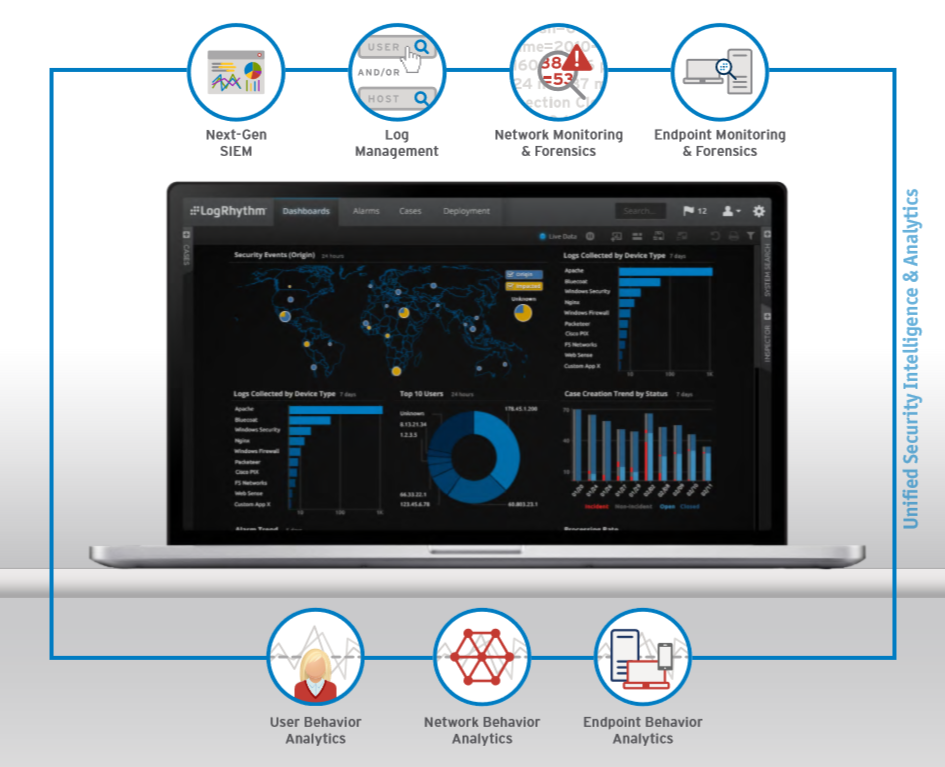
LogRhythm's SIEM may be deployed as an Appliance, Software or Virtual Instance Format. It supports a N-Tier scalable architecture comprising a Platform Manager, AI Engine, Data Processors, Data Indexers and Data Collectors. A consolidated all-in-one deployment is also available.
System Monitor and Network Monitor are options that provide endpoint and network forensic capabilities when deployed. They deliver system process, file integrity and NetFlow monitoring, deep packet inspection (DPI), and full-packet capture.
LogRhythm combines event, endpoint and network monitoring capabilities with User and Entity Behaviour Analytics (UEBA) features, an integrated incident response workflow, and automated response capabilities.
LogRhythm separated out the log processing and indexing capabilities of its SIEM product to form two separate components; added a storage back end based on ElasticSearch to provide an unstructured search capabilities and clustered full data replication.
Other enhancements have included improvements to the risk-based prioritization (RBP) scoring algorithm; additional parsers for applications and protocols for Network Monitor; support for cloud services such as AWS, Box and Okta; and integrations with cloud access security broker (CASB) solutions including Microsoft's Cloud App Security (formerly Adallom) and Zscaler.
Armana believes LogRhythm is an excellent fit for Organizations that require advanced and integrated threat monitoring capabilities within a SIEM solution and for those Businesses that have resource challenged security teams that need a high degree of automation and out-of-the-box functionality.
Product Strengths:
☑ Delivers a SIEM solution with endpoint monitoring, network forensics, UEBA and incident management capabilities to support Security Operations plus advanced threat monitoring and rapid incident responses.
☑ Provides a highly interactive and customizable User experience along with dynamic context integration and security monitoring workflows.
☑ Provides automated response capabilities that can execute actions on remote devices.
☑ From customer feedback, LogRhythm is considered straightforward to deploy and maintain; and provides effective out-of-the-box use cases and workflows.
☑ Wealth of application and professional experience applied and feedback into the technology: taken from LogRhythm's extensive use and diverse installation base.
☑ It is very visible in the competitive SIEM environment and highly regarded during Gartner evaluations.
 CLICK Image to download the LogRhythm's Security Intelligence and Maturity Model White Paper.
CLICK Image to download the LogRhythm's Security Intelligence and Maturity Model White Paper.
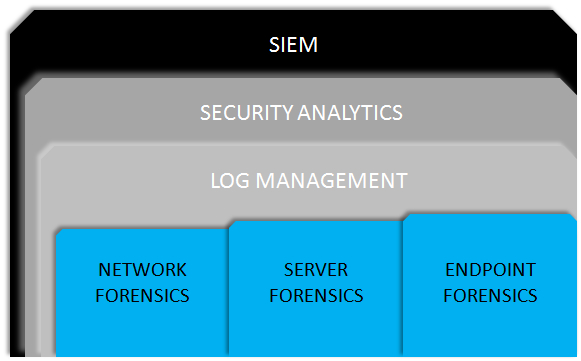
SIEM ... Next-Generation, unified platform for advanced detection & response
LogRhythm's Next-Generation SIEM provides a unified platform, which ensures that the vital capabilities of Security Intelligence are delivered via a fully integrated product suite: with each element designed to elegantly and efficiently work as a whole. This allows Organisations to purchase and deploy the full Suite for complete Cyber Threat Protection or start with specific elements and build (as budget permits) to the complete LogRhythm Cyber Solution. The elements are briefly discussed below with a download access to a datasheet for each.
Security Analytics ...... Holistic threat analytics & compliance automation
Log Management ...... Centralized visibility into all log and machine data, at any scale
Network & Server Forensics ...... Real-time deep packet analytics and full capture
Endpoint Forensics ...... Real-time user, file application and system behaviour monitoring
Collection Element Overview
LogRhythm's collection element allows the aggregation of log data, security events and other machine data. Collectors can operate locally or remotely, can be centrally monitored and managed and are easy to deployment and administer. Scalability is enhanced by the application of load balancing between Data Processors. Data is moved via encrypted & authenticated TLS communications and can be compressed for effective bandwidth utilization.
Collectors can be configured for unidirectional network communication paths, supporting classified environment and regulatory compliance needs. Furthermore they ensure data integrity during a network interruption by intelligently spooling volatile UDP traffic and tracking state for non-volatile data. Resilience is buttressed through automatic failover between Data Processors.
 CLICK Image to download the LogRhythm's Full Collection Technology Product Overview.
CLICK Image to download the LogRhythm's Full Collection Technology Product Overview.
End-point Monitor Element Overview
A key component of the Cyber Protection Process is the ability to correlate what's happening at the endpoint throughout the IT Infrastructure. LogRhythm delivers integrated, overall visibility and protection via Endpoint Monitoring and Forensics.
N.B. Correlating network-wide event data with activities occurring on the endpoint is often hindered because endpoint-based activities can not be consistently logged and often require multiple solutions to fill the information gaps.
LogRhythm's Endpoint Monitoring & Forensics provides independent awareness and insight into what's happening on an endpoint. It provides a superb layer of protection from a broad spectrum of problems, ranging from operational events such as system and application failure to security and compliance violations linked to unauthorized or malicious activity. It's centrally managed as a fully integrated component of LogRhythm.
Endpoint Monitoring and Forensics includes:-
♦ Independent logging of critical endpoint activity ♦ Detection of changes made to the Windows startup registry ♦ Comprehensive event detail ♦ Protection from zero-day attacks and critical failures ♦ Prevention of unauthorized data transfers ♦ Full integration with all event data for true correlation and event context.
 CLICK Image to download the LogRhythm's Full End-point Monitor Product Overview.
CLICK Image to download the LogRhythm's Full End-point Monitor Product Overview.
Network Monitor Element
LogRhythm Network Monitor provides enterprise-wide network visibility in more detail than traditional network and security solutions, i.e. flow analysis tools and next-generation firewalls. It's deep insight helps Organizations detect and respond to Advanced Cyber Threat, including nation-state espionage, zero-day malware, and data exfiltration.
Achieved through:- ♦ Application Identification ♦ SmartFlow Session Classification ♦ Deep Packet Analytics (DPA) ♦ Full Packet Capture ♦ SmartCapture™ ♦ Unstructured Search with Drill Down ♦ File Reconstruction ♦ Alerts and Dashboard ♦ API Integration
LogRhythm Network Monitor is an Out-of-Band deployment that has no impact on network device capacity and performance.
 CLICK Image to download the LogRhythm's Network Monitor Product Overview.
CLICK Image to download the LogRhythm's Network Monitor Product Overview.
Processing and Indexing Data Tiers Element
LogRhythm's data processors receive machine data from the collection tiers and process it into a contextual format for the purpose of Analytics. They operate across petabytes of heterogeneous machine data. Data processors normalize and categorize the wealth of data obtained from many different products and vendors to create and deliver a consistent Machine Data Intelligence Fabric (MDI) for both machine-based and search-based Analytics. This MDI Fabric includes a large set of metadata fields that are refined to essential context: including factors such as event criticality, impacted host, and host origin.
Collected data is securely sent to the data processor, where it is parsed and normalized into contextual metadata, which is then forwarded to the AI Engine for machine-automated security analytics, and, to the Data Indexer providing the reference for unstructured searches. Furthermore, a copy of every raw message is forwarded to an Archive. N.B. Archived messages can be recalled, re-processed, and added back into the indexing tier for forensic analysis.
 CLICK Image to download the LogRhythm's Data Processing-Indexing Technical Brief.
CLICK Image to download the LogRhythm's Data Processing-Indexing Technical Brief.
Precision Search Element
LogRhythm's Search expedites incident detection and response through fast analysis and a deeper understanding of critical event factors. It is an intuitive web console that is designed to provide security workflows and to simplify searches through a single, easy-to-use interface. It delivers a powerful combination of contextualized and unstructured searches. A highly-performant, Elasticsearch indexing tier delivers immediate and precise results for any scale of deployment.
Functions include:- ♦ Unified Search Interface ♦ Intuitive, Advanced Search Builder ♦ Unstructured Search ♦ Clustering ♦ Contextualized Search ♦ Machine Data Intelligence
 CLICK Image to download the LogRhythm's Precision Search Product Overview.
CLICK Image to download the LogRhythm's Precision Search Product Overview.
Threat Intelligence Ecosystem Element
LogRhythm's Threat Intelligence Ecosystem is the industry's first "collective" of threat intelligence partners and open source providers focused on delivering security intelligence via the next-generation Security Intelligence Platform.
By integrating the massive amount of Threat Data provided by the Ecosystem Partners and Open Source Providers with the Machine Data collected by LogRhythm throughout the Organisation; highly contextualized security intelligence is established that in turn produces rapid and accurate threat detection and responses to cyber attacks.
 CLICK Image to download the LogRhythm's Threat Intelligence Ecosystem Product Overview.
CLICK Image to download the LogRhythm's Threat Intelligence Ecosystem Product Overview.